You Spoke, We Listened—the Updated Astra IAM Experience is Here!

In early March, we introduced serverless Astra DB. Since then, we’ve gotten some valuable feedback from our users, and we’re excited to offer an improved, refined experience for your identity and access management (IAM) needs. Here’s how we’re making it easier to manage custom roles, application tokens, and user access.
More default roles
Our mission is to make it as easy as possible to quickly and securely connect to a database—so we’ve added more default roles. Just pick the one that works best for your use case!
For example, you might want to create a token that grants API read-only access for all databases in your organization. Under Organization Settings in the Token Management area, you'll now be able to create a token and assign it the "API Read Only User" role. Selecting this will return the correct set of permissions for that use case.
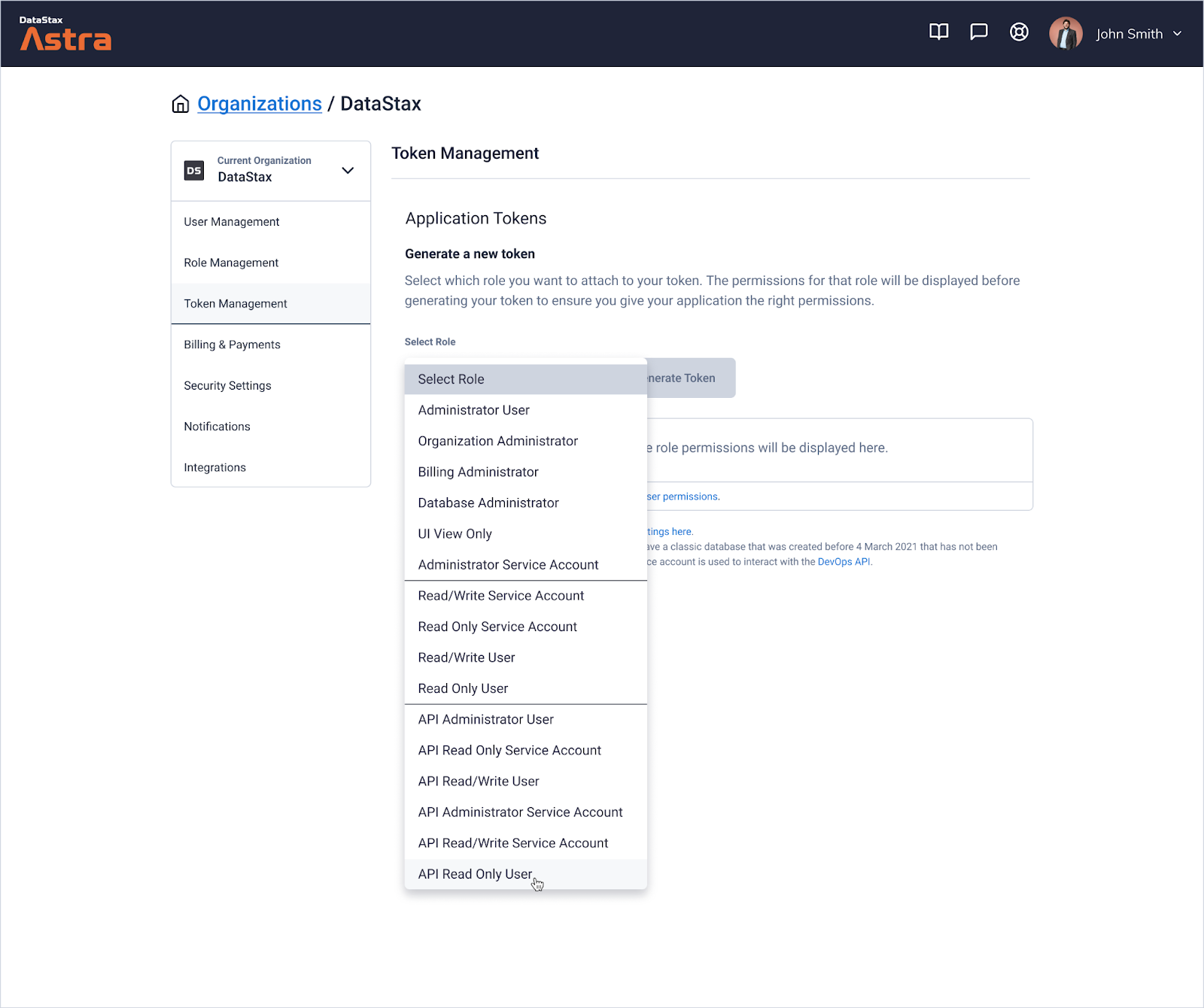
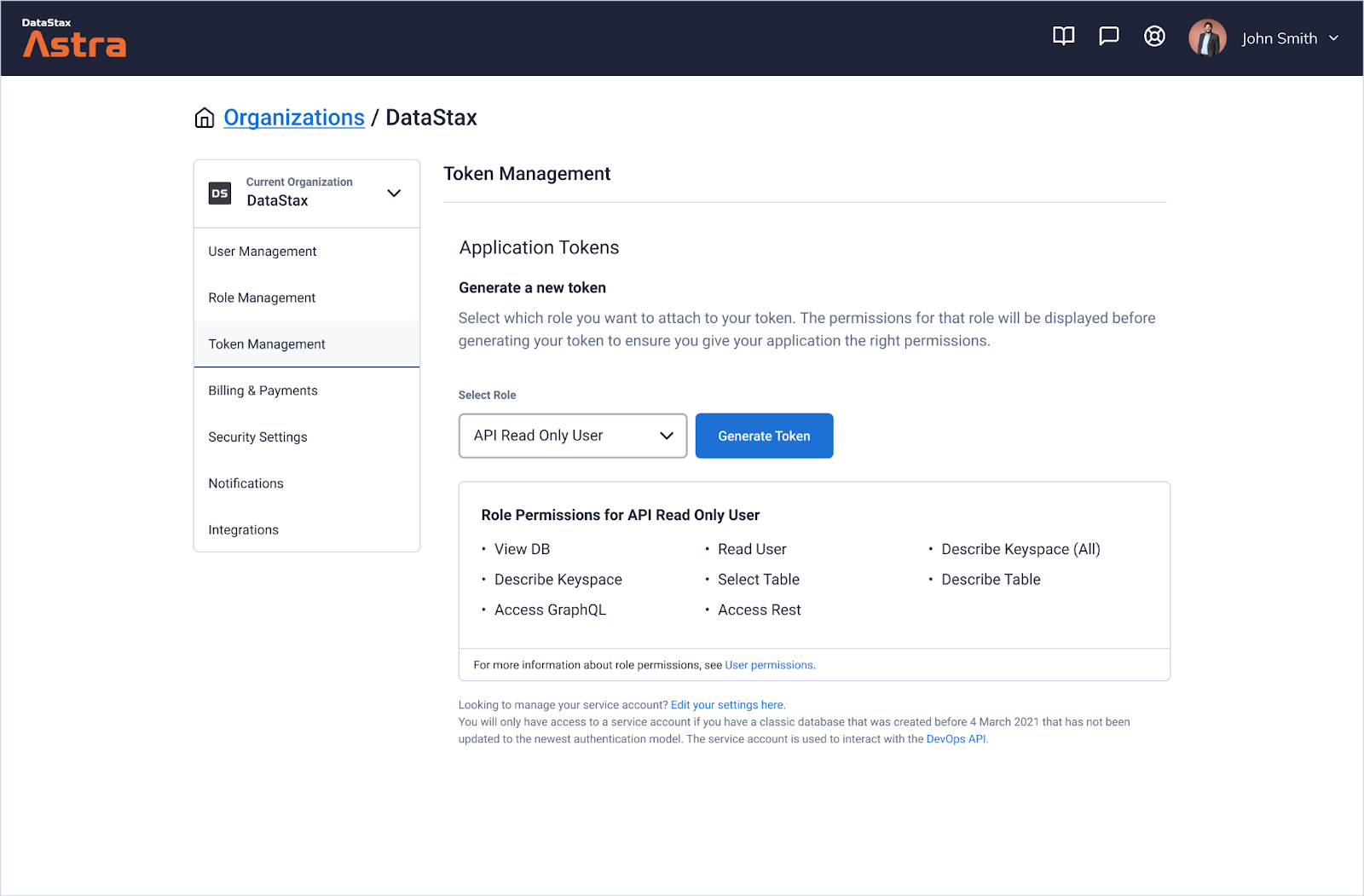
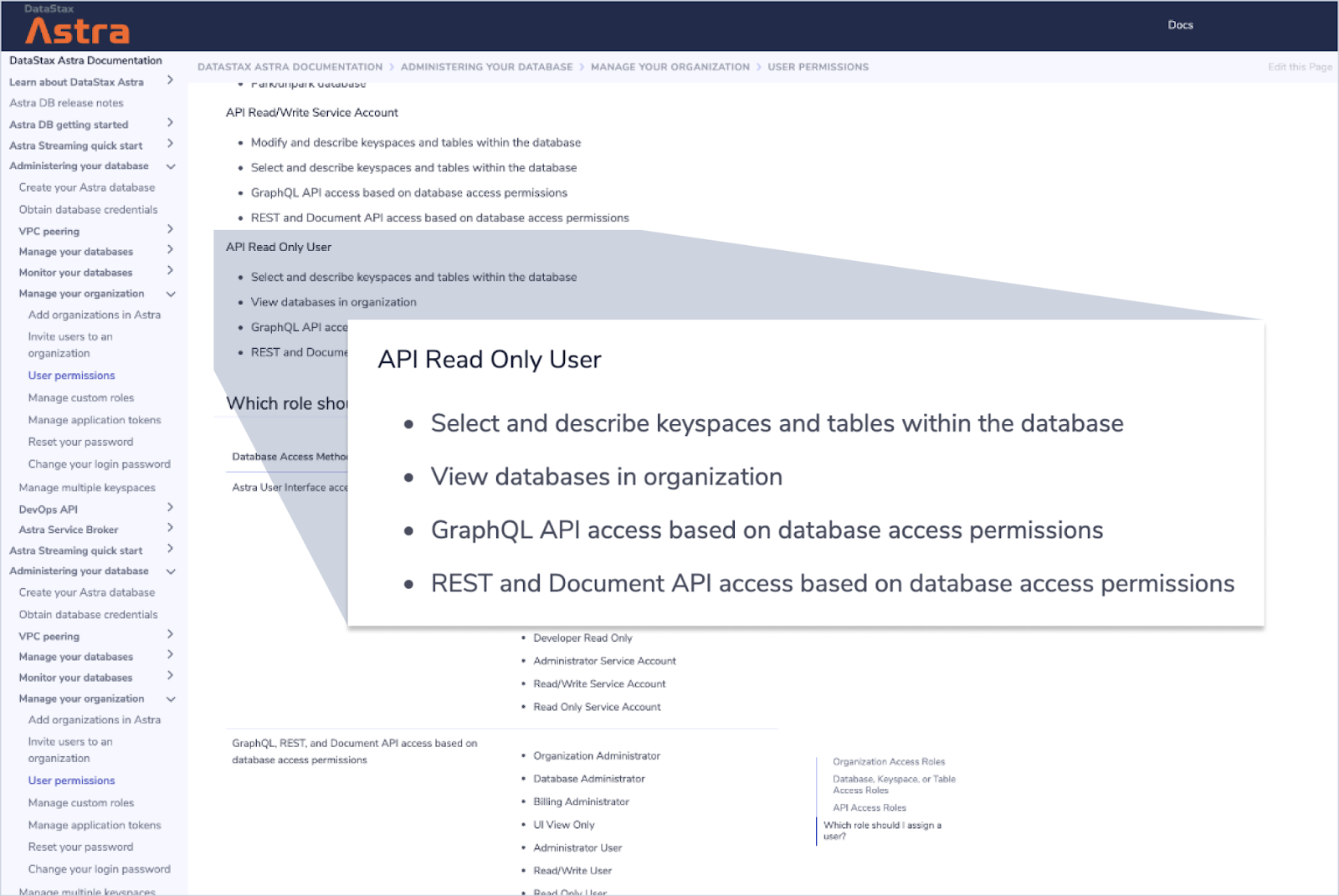
From here, you'll also find a link to our new and improved documentation that will provide you with more details for each role and permission.
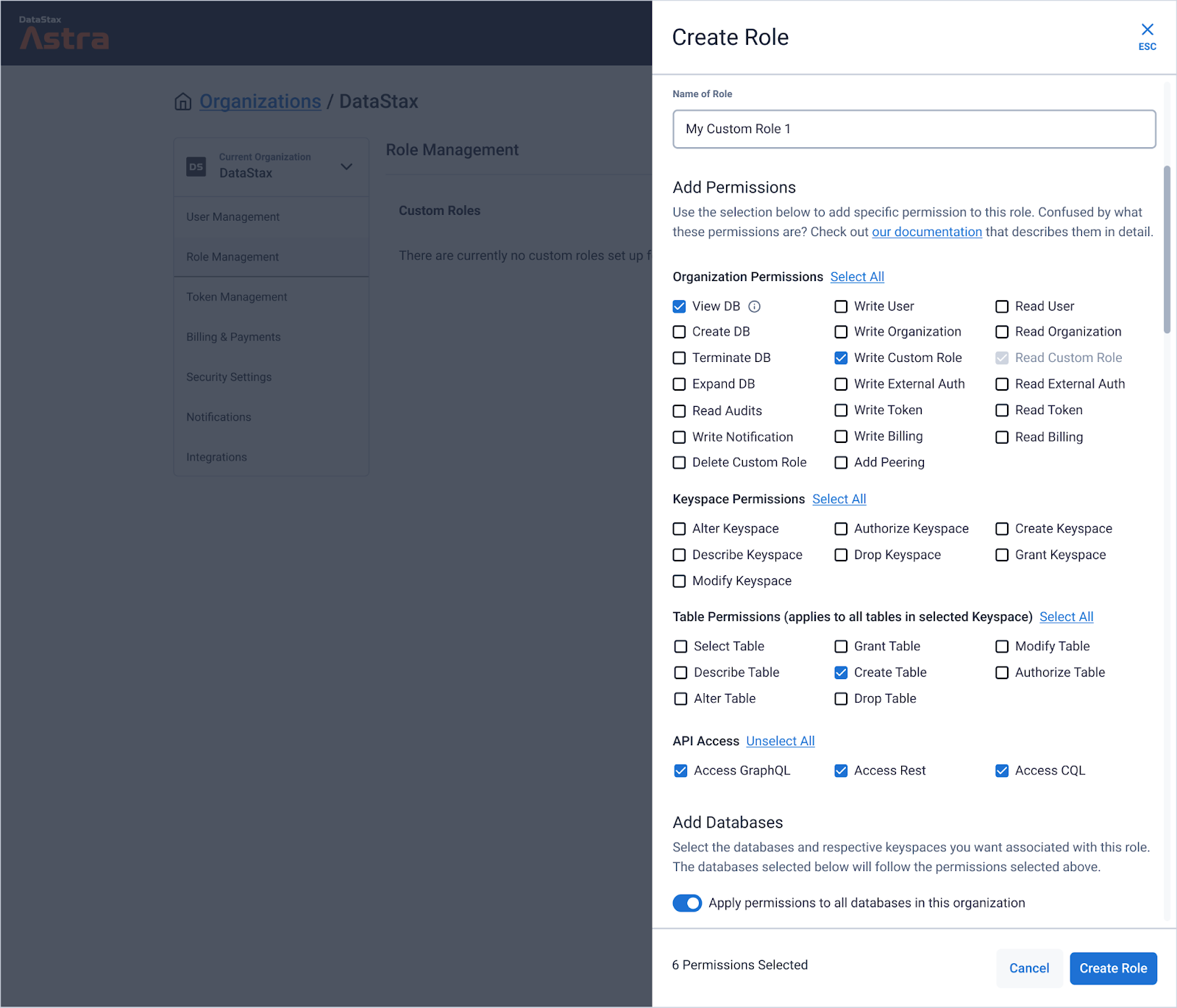
Updated custom role experience
With custom roles, you can scope permissions for real users and application tokens to the entire organization, specific databases, keyspaces, or tables without using CQL. Quickly get going by creating custom roles within Role Management in your Organization Settings, or with our easy-to-use DevOps API.
Application tokens
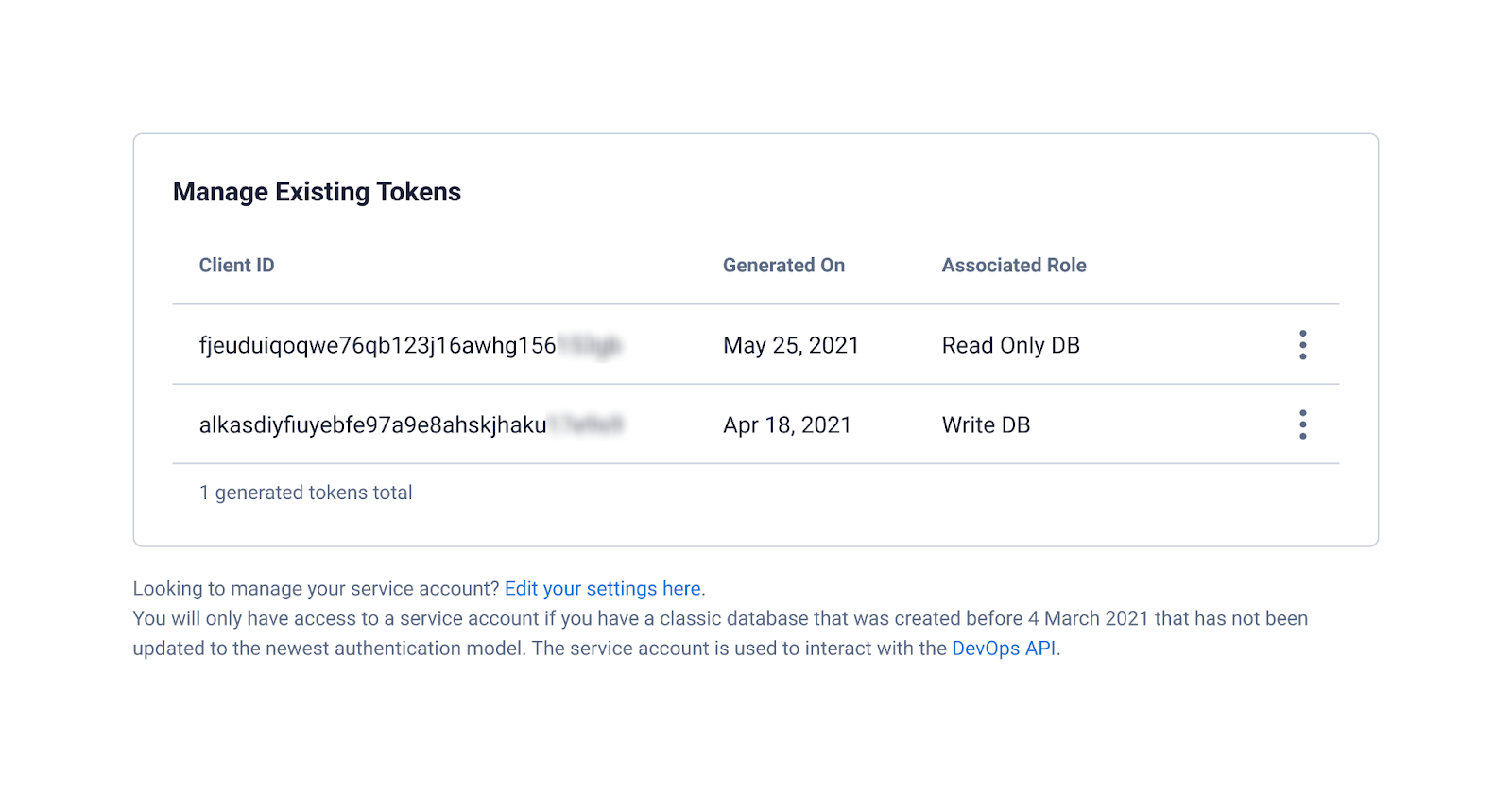
Managing application tokens is done at the organization level so you can easily view and manage all tokens in one place. This also enables you to create an application token that can be used to generate databases within your organization.
When an application token is generated, a corresponding client ID and client secret is also generated. For increased security, values for token, client ID, and client secret are all available for copy or download only once, upon generation. These tokens do not automatically expire, but can be destroyed in case they are compromised or no longer needed.
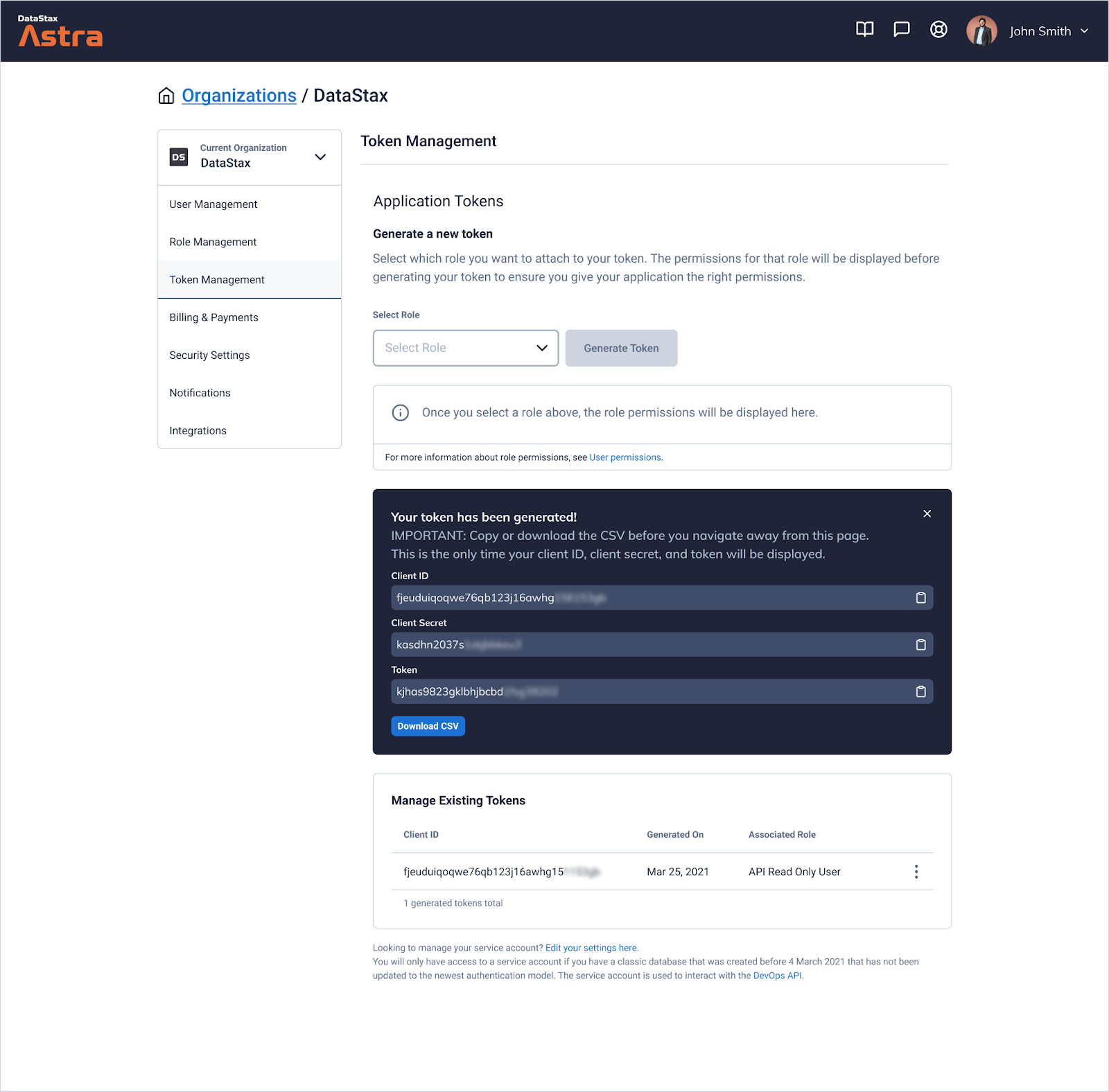
Client ID and client secret are used to authenticate against databases created on or after March 4, 2021 (when serverless Astra DB was launched), in lieu of username and password. We moved application tokens under Organization Settings to open up opportunities for more granular control of authorization within each database. For example, one token may be used only for reading a specific database while another token may have authorization to write to the same database. Following principles of least-privileged access increases the security of your database by reducing your exposure.
Managing roles, tokens, and users with the DevOps API
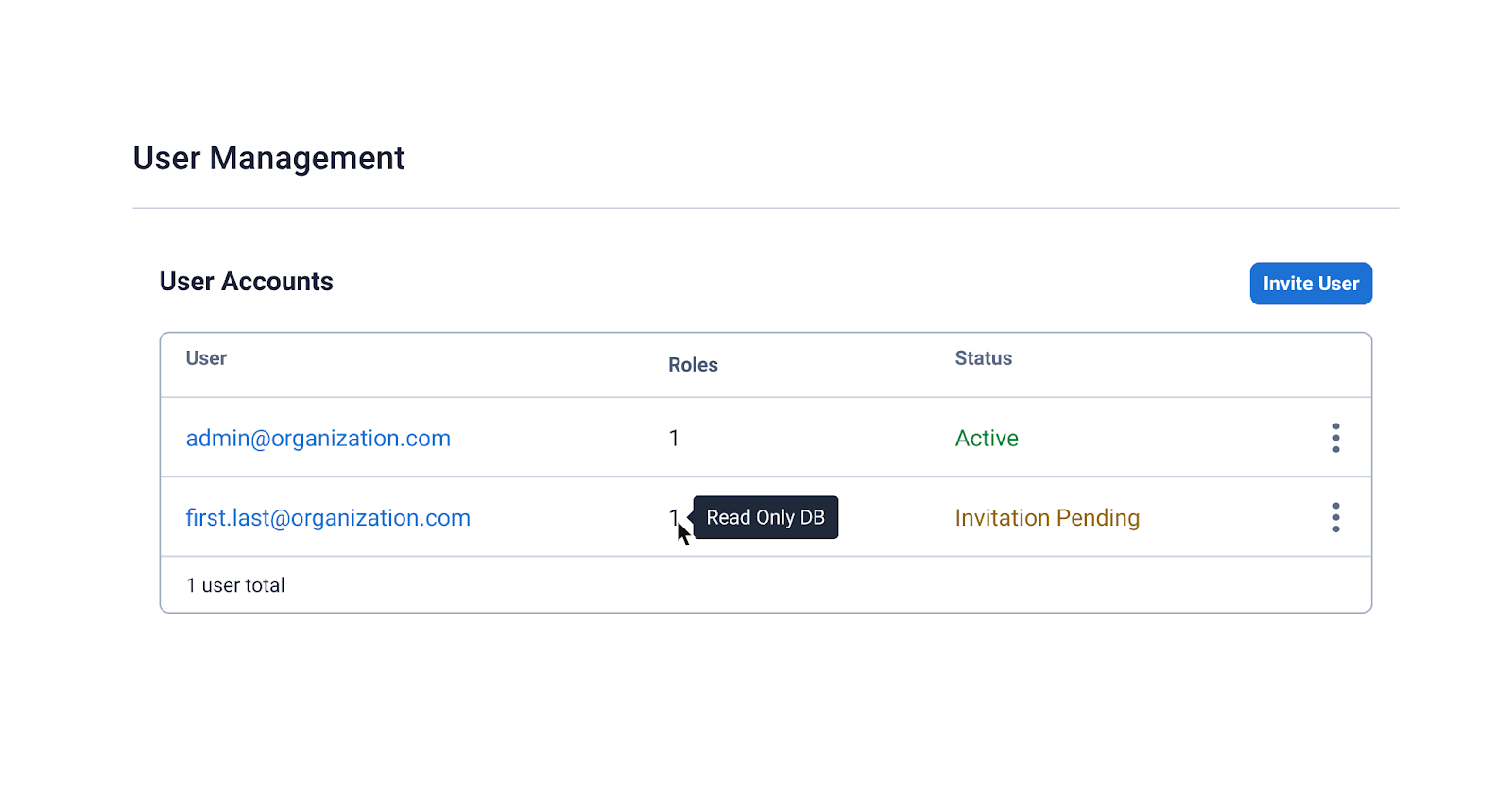
You can create and manage custom roles, application tokens, and organization users within Astra itself or the DevOps API. Any roles, tokens, or users created or updated with the DevOps API will also show up in the Astra interface. You get the best of both worlds: the ability to automate authentication and authorization management and the ability to easily audit or make quick changes.
A secure database in the cloud
We are continuously evolving Astra at a rapid pace to make it the easiest, and most secure, Database-as-a-Service offering on the market. Keep the feedback coming—and if you’re not an Astra user, we welcome you to use Astra for free.




